End-to-End Embedded BI Deployment Guide
Embedded Business Intelligence (BI) stands out as a crucial component for enhancing business applications with analytical capabilities. This whitepaper explores the journey of deploying an Embedded BI solution, detailing the strategic planning, selection, development, and continuous improvement phases necessary for successful implementation.
Aimed at decision-makers and IT leaders, it provides a comprehensive guide to navigating the challenges and leveraging the opportunities of integrating BI into existing business ecosystems, ultimately fostering a data-centric culture.
Here’s what is covered in our guide:
- Planning phase: Lay the groundwork for your BI deployment – define objectives, identify your audience, and more.
- Selection phase: Thoroughly evaluate potential vendors and make informed decisions on partnering with a BI vendor.
- Development phase: Implement and customize the BI solution. Connect to your data sources and more.
- Data security and governance: Ensure compliance with industry regulations.
- Deployment phase: Prepare for the successful launch of your BI solution.
- Post-deployment phase: Learn how to maintain the effectiveness of your BI solution.
- Continuous improvements: Get an idea of how to drive ongoing enhancements.
Continue Reading
Fill out the form to continue reading.
Planning Phase
The planning phase serves as the foundation of a successful embedded BI deployment. During this first phase, you lay the groundwork for your entire journey, ensuring that your objectives are clearly defined and aligned with your organizational goals.
Define Objectives
Start by clearly defining your objectives for implementing embedded BI. Clearly outlining your objectives is paramount as it sets the trajectory for your embedded analytics evaluation.
The choice of the deployment model is pivotal in fulfilling your objectives effectively. Consider the following to identify the most suitable embedded BI solution for your organization:
- Assess the Need for Different BI Solutions: Determine whether a Software Development Kit (SDK), a hosted solution, or a hybrid approach best meets your needs. This decision hinges on how you plan to integrate and use BI functionalities within your existing systems.
- White-Label Solutions: Decide if a complete white-label solution is necessary for your use case. A white-label solution allows you to brand the BI tool as your own, providing a seamless user experience that reflects your brand identity.
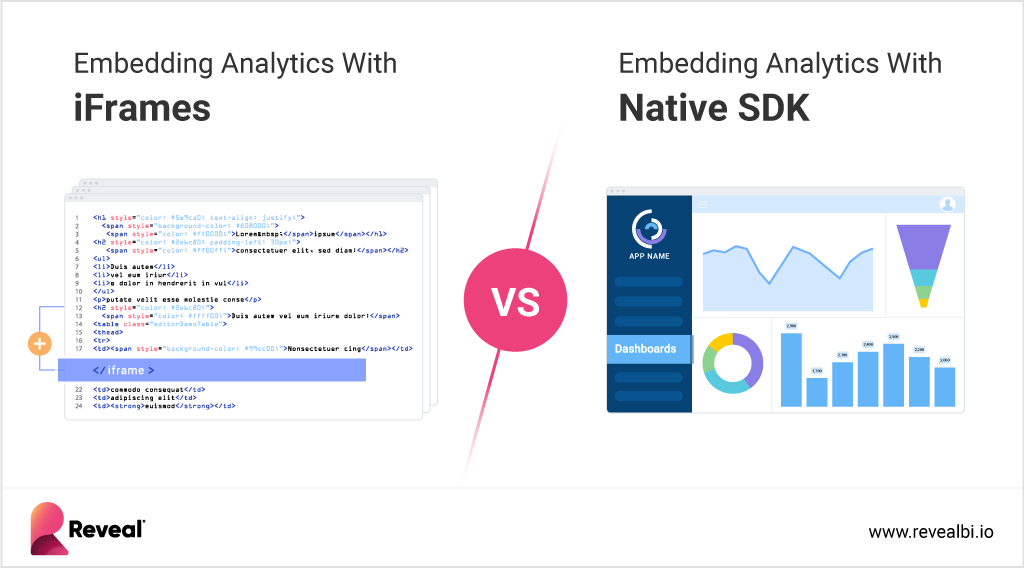
- iFrame vs. Embedded White-Label Solutions: Evaluate if an iFrame solution suffices for your integration needs or if a more integrated, embedded white-label solution is necessary. The choice depends on the level of customization and integration you require.
- Development Team Availability: Consider whether your organization has the in-house development resources to integrate and maintain the BI solution. This will influence the choice between a more turnkey hosted solution and one that requires significant custom development work.
Identify Your Audience
Understanding your audience’s specific needs and capabilities is crucial for customizing the BI solution to provide maximum value. The user base for embedded BI systems often spans a spectrum from non-technical to highly technical users, each requiring different features and interfaces.
Non-Technical Users
- Profile: These users typically lack a background in data analysis or IT but need to access insights and reports to inform their decision-making. They prioritize ease of use and clear, actionable information over complex analytical capabilities.
- Solution Requirements: For non-technical users, the embedded BI solution must be user-friendly, with intuitive navigation and simple interactions like drag-and-drop. The interface should be straightforward, minimizing the learning curve and enabling quick access to relevant data and insights.
Technical or Power Users
- Profile: This group consists of users with advanced data analysis skills and a deep understanding of technical systems. They are responsible for creating, editing, and managing detailed dashboards and reports, diving into complex data sets, and optimizing data models for enhanced performance and accuracy.
- Solution Requirements: Power users demand robust, advanced analytics features and extensive customization capabilities. The BI solution should support complex report generation, deep data exploration, and the ability to tailor visualizations and analytics processes to meet specific needs.
Define Deployment Scope
Determine the scope of your deployment, whether the deployment will be internal (for use within your organization), external (for clients outside your organization), or a hybrid of both. This clarity ensures that you allocate resources effectively and prioritize features that align with your deployment objectives.
Integration with Existing Systems
- Internal Use: Assess whether the BI solution needs to integrate with existing internal applications or platforms. This integration is crucial for enhancing decision-making processes within the organization, facilitating seamless access to analytics and reports directly from the existing IT ecosystem.
Cloud-Based vs. On-Premises Solutions
- SaaS Cloud Deployment: For a SaaS (Software as a Service) model, the BI solution is hosted in the cloud, offering the advantage of accessibility from anywhere via the internet. This option reduces the need for extensive on-premises infrastructure, offering scalability and ease of maintenance.
- On-Premises Deployment: Choosing an on-premises deployment means the BI solution will be installed and run on the organization’s own servers. This model provides more control over the data and system, higher customization options, and potentially enhanced security, but it requires significant on-site management and maintenance.
Select KPIs
Selecting the right Key Performance Indicators (KPIs) is a pivotal step in the planning phase, as KPIs serve as benchmarks for the success of the embedded BI deployment. They enable organizations to quantify progress toward their objectives and refine their strategies based on data-driven insights.
Identification of Critical Measurements
- Relevance to Objectives: KPIs should be directly linked to the organization’s strategic goals and objectives. This alignment ensures that the metrics tracked are relevant and contribute to the overall success of the BI initiative.
- Driving Decisions: Choose KPIs that empower users to make informed decisions. This involves selecting actionable metrics that provide insights that can lead to meaningful changes in business strategies or operations.
Audience-Centric KPI Selection
- User Needs and Preferences: Different user groups within the organization may require different sets of KPIs based on their roles and responsibilities. Understanding these needs is crucial to ensure that each user has access to the most relevant and impactful metrics.
- Accessibility and Visibility: Determine which KPIs need to be prominently displayed for each audience group. Strategic placement of these metrics within the BI tool can enhance their visibility and ensure they are consistently monitored and acted upon.
Data Source Identification
Begin by compiling a comprehensive list of all data sources that will be connected to your BI system. This includes databases, applications, APIs, and other data sources that contain valuable information for analysis. Thoroughly identifying and understanding your data sources is crucial for ensuring data quality and extracting comprehensive insights from your embedded analytics solution.
- List All Data Sources: Compile an complete list of data sources, including databases, applications, APIs, and other repositories that hold relevant data. This list should encompass all potential sources of data that the BI system will need to access for analysis.
- On-Premises vs. Cloud: Ascertain whether your data sources are hosted on-premises or in the cloud. This distinction is important for understanding the data integration mechanisms and security measures that need to be in place. Cloud-hosted data sources might offer more scalability and accessibility, while on-premises sources might require more robust internal network security.
- Type of Data Sources: Classify each data source based on its nature and type, such as traditional relational databases, NoSQL databases, REST endpoints, or file-based data stores. This classification helps in determining the appropriate integration method and tools for each data source.
- Data Readiness for Analysis: Assess whether the data from these sources is in a format that can be readily used for analytics and dashboard creation. This includes evaluating the need for data cleaning, transformation, or aggregation to ensure the data is actionable and suitable for end-user consumption and analysis.
Budget Assessment
Determine the budget for the BI project, including software, hardware, training, and maintenance. This financial planning ensures that all aspects of the BI deployment are feasible and sustainable over time.
- Upfront Implementation Costs: Consider the initial expenses associated with the deployment of the BI solution. This includes the cost of software acquisition, hardware (if opting for an on-premises solution), and any additional infrastructure required for setup and integration.
- Long-Term Operational Expenses: Beyond the initial setup, anticipate the ongoing costs of operating and maintaining the BI system. This encompasses software licenses, maintenance fees, hardware upgrades (as necessary), and ongoing staff training to ensure they can use the BI tools effectively.
- Alignment with Financial Resources: Select a pricing model that aligns with your organization’s financial capacity and usage expectations. The chosen model should accommodate fluctuating needs and scalability concerns without causing budgetary strain.
- Common Pricing Models
- Fixed-Price: A one-time fee that covers the BI solution, often suited for organizations with predictable usage patterns.
- Pay-Per-User: Charges based on the number of users accessing the BI system are beneficial for companies with a clear count of BI tool users.
- Pay-Per-Editor: Costs depend on the number of users with permission to create and edit reports, which is ideal for organizations where only a subset of users will need advanced functionalities.
Selection Phase
The selection phase is crucial. Choosing an embedded BI vendor that aligns with your objectives and needs is a challenging task. There are many vendors on the market, but by following the previous step, you should have been able to narrow the options.
So, now that you have a few vendors you are interested in, take the time to assess their compatibility with your tech stack, product capabilities, and alignment with your organization’s objectives, scope, KPIs, and budget.
To make the critical decision of who to partner with, follow these steps:
Vendor Research
Conducting thorough research on potential vendors is crucial for any business looking to make informed decisions. This process involves gathering information on the vendors’ products, services, reputation, and pricing to evaluate their suitability for the organization’s needs.
- Maturity of the BI Solution: Evaluate the solution’s development stage, its market presence, and its proven effectiveness in similar organizational contexts.
- Support Infrastructure: Investigate the vendor’s support mechanisms, including the availability of technical assistance, response times, and the quality of service.
- Reputation Analysis: Examine customer testimonials, reviews, and case studies to assess the vendor’s reliability, customer satisfaction, and success in deploying BI solutions.
- Company Background: Study the vendor’s history, growth trajectory, leadership stability, and financial health to gauge long-term viability and reliability.
API and SDK Evaluation
Assess if the selected BI tool’s API/SDK seamlessly integrates with your existing technical stack to ensure compatibility and a smooth integration process.
- Tech Stack Compatibility: Confirm that the vendor’s BI solution can integrate with your organization’s existing cloud/SaaS platforms, desktop environments, and web frameworks.
- Backend Integration: Evaluate how well the BI solution integrates with server technologies like NodeJS, Java, or .NET Core, ensuring smooth backend operations.
Development Languages
Compatibility with popular development languages is essential for facilitating seamless customization and extension of the BI solution to meet your organization’s specific requirements.
- Language Support: Verify that the BI solution supports widely used languages such as C#, JavaScript, and TypeScript, facilitating customization and integration with existing systems.
Documentation
Comprehensive documentation is fundamental for facilitating smooth implementation, customization, and ongoing maintenance of the BI solution. High-quality documentation, tutorials, training videos, etc., ensure clarity, accessibility, and ease of reference for developers.
- Comprehensive Guides: Ensure the vendor offers detailed how-to guides, API documentation, and feature demos in languages and formats accessible to your development team.
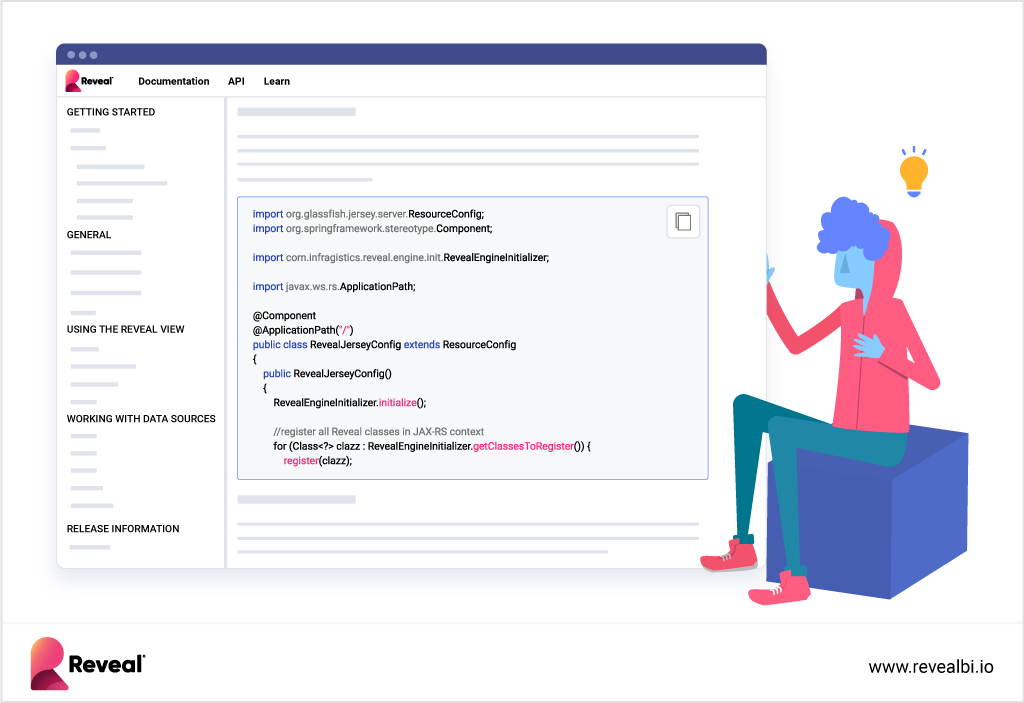
Training
Effective training and support are essential for maximizing user adoption and ensuring users leverage the BI solution to its full potential.
- Training Programs: Determine if the vendor provides comprehensive training modules and academies to equip users with the necessary skills and knowledge.
- Advanced Learning: Check for the availability of in-depth sessions with the product team to understand advanced features and customization options.
Feature Comparison
The features of a given vendor might be the factor you choose to partner with or not. You should look for features aligned with your organization’s unique objectives, industry requirements, and long-term strategic goals. For example, suppose you’re in the retail industry and want to predict future demand and inventory levels. In that case, you need a BI solution that provides predictive analytics features such as time series forecasting and machine learning.
Nevertheless, a vendor’s commitment to improving and expanding its features is equally important. So, make sure you ask and look for:
- Roadmap: Public and easily accessible roadmaps provide visibility into future feature enhancements and development plans and allow you to assess the vendor’s commitment to innovation and alignment with your organization’s evolving needs.
- Prior release notes: Reviewing prior release notes allows you to gain insights into the vendor’s track record of feature enhancements, bug fixes, and performance improvements.
- Release cadence: Regular updates and timely feature releases demonstrate the vendor’s responsiveness to customer feedback and commitment to product improvement.
Demo & PoC Testing
Requesting demos and conducting proof-of-concept (PoC) testing enables hands-on evaluation of the BI solution’s usability, functionality, and suitability for your organization’s needs. This stage of the selection phase allows stakeholders and developers to assess the BI solution in real-world scenarios and make informed decisions.
- Comprehensive Demos: Ensure overview and technical demos are available to get a well-rounded view of the BI solution.
- Proof of Concept: Conduct PoC testing with relevant stakeholders to evaluate the solution’s practical application and effectiveness in your operational context.
Select a Vendor
At this point, you should be able to make a decision based on various factors, including pricing, features, security, support, and scalability. Choose a vendor that aligns with your organization’s long-term vision and strategic objectives and demonstrates a commitment to partnership, innovation, and ongoing collaboration to support your evolving BI needs.
Development Phase
The development phase is when your analytics solution starts to take shape. It focuses on implementing and customizing the chosen BI solution to meet your organization’s specific needs and requirements.
There are four stages to this phase – data integration, data security, customization, and performance testing. Going through them all successfully is paramount for the solution’s deployment. Here are the things you should focus on for each of these stages:
Data Integration
The first stage of the development phase involves connecting the BI solution to various data sources to ensure data quality, consistency, and accessibility for insightful analytics.
- Make sure that the chosen solution is compatible with your various data sources without the need for extensive coding.
- To ensure secure and reliable data access, evaluate the solution’s data connectivity capabilities to integrate with your current security scheme seamlessly.
- Ensure that it supports integration with multiple data sources simultaneously, allowing for comprehensive data analysis and reporting across different datasets.
Data Security
The next phase of the deployment process focuses entirely on data security, but you should keep the protection of your data in mind during this phase, too. As you are working to develop the solution and align it with your organization’s needs, consider this:
- Identify whether the BI solution offers role-based access control that allows administrators to define granular access permissions based on user roles and responsibilities.
- Ensure the client and server can be further secured according to your security policies.
- Verify that there are multiple checkpoints for data security in the API lifecycle.
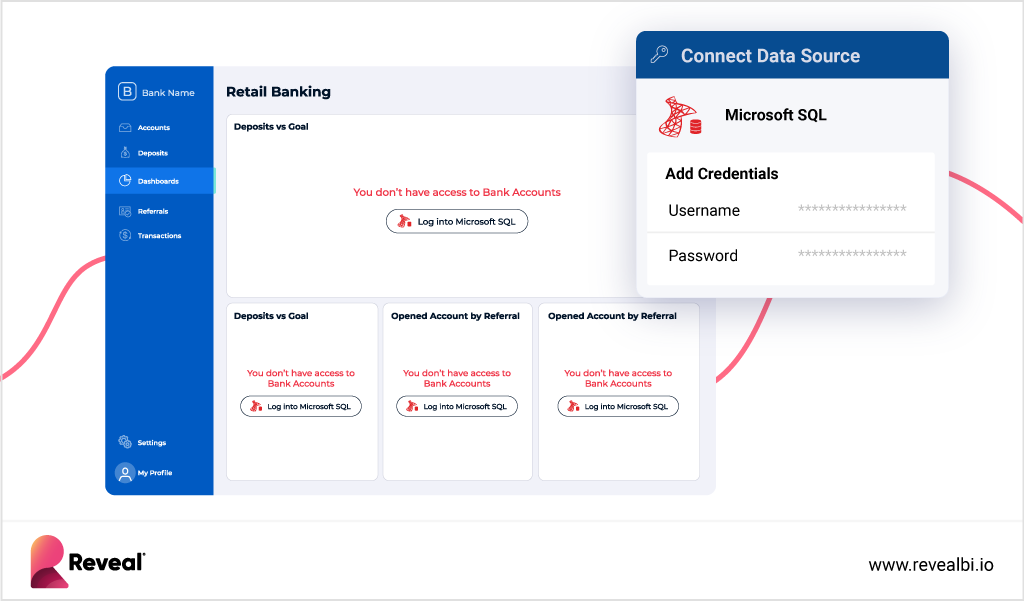
UX/UI Customization
Customizing the BI solution’s user interface (UI) is essential for creating a cohesive and intuitive analytics experience that aligns with your organization’s brand and enhances user adoption. To achieve this, the BI solution should offer more than the ability to change the colors of the buttons.
- Ensure the BI solution offers customization options to match the embedded solution to your brand experience, including color schemes, logos, and branding elements, to maintain brand consistency across applications.
- Determine whether the BI solution supports customer-specific customization per deployment, allowing for tailored UI/UX experiences based on individual customer requirements and preferences.
- Review the availability of UX APIs that enable/disable interactions on the client UI. These APIs provide developers with the flexibility to customize and extend the user experience based on specific use cases and requirements.
Performance Testing
Ensure the chosen BI solution meets performance benchmarks and delivers a seamless user experience even under heavy workloads.
- Ask the vendor if it provides technical guidance and best practices for optimizing the performance of the BI solution.
- Review whether the vendor customers are representative of your performance needs.
Data Security and Governance
Once you reach this phase, your focus should be on safeguarding your data and ensuring compliance with relevant industry regulations. To ensure alignment with regulatory requirements, begin by conducting a thorough assessment of the embedded BI vendor’s data security practices, policies, and infrastructure.
Here are some things to look for when assessing the vendor’s security:
- GDPR Compliance: Make sure the vendor’s security policies and practices align with the General Data Protection Regulation (GDPR) requirements. Ensuring GDPR compliance underscores your commitment to safeguarding user data privacy within the European Union and the European Economic Area.
- CCPA Regulations: Verify the vendor complies with the California Consumer Privacy Act (CCPA) regulations, particularly if your organization conducts business in California or deals with Californian residents’ data. CCPA mandates transparency in data collection practices and provides consumers with control over their personal information.
- SOC2 Compliance: SOC2 compliance is a crucial benchmark for evaluating a vendor’s commitment to data security and integrity. Confirm the vendor can provide evidence of Service Organization Control (SOC2) compliance certificates, demonstrating their adherence to the American Institute of Certified Public Accountants (AICPA) standards.
Security is of essential importance for anything data-related, especially embedding a BI solution into your business applications. These security certificates are fundamental, but there is more you need to look for to assess the vendor’s security and governance commitment.
These are some additional security measures that you should require:
- Data Encryption: Encryption protocols for data transmission and storage ensure that sensitive data remains unintelligible to unauthorized parties, mitigating the risk of data breaches.
- Role-based Access APIs: Role-based access control is an essential security measure that dictates what actions users can perform within the BI solution based on their roles or responsibilities. APIs supporting role-based access control enable administrators to effectively define and manage user roles. This ensures that each user has access only to the data and functionalities necessary for their specific role, reducing the risk of unauthorized data manipulation or viewing.
- Data source-level Authentication Features: Ensuring robust authentication mechanisms at the data source level is foundational for securing data integrity within an embedded BI solution. The solution should support various authentication methods, including username and password for secure credential-based access, tokens for enhanced security, and OAuth for facilitating secure, delegated access to data sources through industry-standard authentication protocols.
- Security Breaches Practices: Does the vendor have a well-defined action plan in case a security breach or data incident occurs? According to Reveal’s Annual Survey Report, security threats are surging and are among software developers’ key challenges. Thousands of cyberattack attempts happen every day, so you need to know you’re in good hands if someone attempts to access your business or user’s data. A well-defined action plan facilitates prompt detection, containment, and resolution of security incidents, minimizing potential damages and ensuring regulatory compliance.
Deployment Phase
The deployment phase marks the transition from planning and preparation to actual implementation. This phase involves configuring servers, databases, and security settings to ensure a well-prepared environment for a successful deployment.
Action steps for this phase:
Vendor Proof of Concept (PoC)
Begin the deployment phase by starting a Proof of Concept (PoC) to explore the vendor’s solution and its availability to tailor to your unique needs and requirements. The PoC process serves as a foundational framework, allowing you to glimpse into the potential of the BI solution within your application’s context. During the PoC, you can start building and customizing the solution and assess its suitability and compatibility with your data sources and infrastructure.
- Use every opportunity to engage in collaborative discussions with the vendor, leveraging their expertise to clarify your organization’s objectives, challenges, and how the BI solution can effectively address them.
- Make sure to engage the stakeholders at every stage of the PoC development process, offering them a tangible demonstration of the BI solution’s capabilities and potential impact.
- Ensure that you can schedule weekly check-in calls with the vendor to review progress, address any concerns, and make adjustments as necessary.
- Confirm that the vendor provides a dedicated support team to assist your development team at every step of the process.
Containerized Deployment with Docker or Kubernetes
Determine whether the BI solution can be deployed using containerization technologies such as Docker or Kubernetes. Containerization offers numerous benefits for deploying BI solutions, including improved consistency, scalability, and resource efficiency.
- Verify if the BI solution architecture and dependencies are conducive to containerization.
- Check if Docker or Kubernetes clusters can provide the necessary features to ensure uninterrupted access to the BI solution, even in the event of node failures or maintenance activities.
Integration with Existing Applications
Integration with existing applications is a critical consideration during the deployment phase of a BI solution to ensure seamless compatibility and data synchronization between the BI solution and your existing applications.
- Explore options for integrating the BI solution with your existing applications or systems, such as ERP, CRM, or custom-built applications.
- Check whether the BI solution offers APIs or connectors for seamless integration with third-party applications and services.
- Assess the BI solution’s ability to transform and manipulate data to match the requirements of existing applications, ensuring consistency and accuracy across integrated systems.
Post-Deployment
Post-deployment is about ensuring the ongoing success of your embedded BI solution, including user training, support, monitoring, and keeping the BI tool up to date with the latest features and security patches.
Here are the action items for this phase of the deployment process:
Updates & Upgrades
Ensure the vendor provides regular, consistent updates to the BI tool, including bug fixes, performance improvements, and new features.
- Maintain a schedule for receiving and integrating consistent updates from the vendor.
- Establish procedures for integrating updates into your existing deployment, minimizing disruptions, and maximizing the utilization of new functionalities.
- Seek user feedback to guide the prioritization of updates, ensuring alignment with evolving business needs and user expectations.
Security
Confirm that the vendor promptly releases security patches to address vulnerabilities and mitigate security risks within the BI solution.
- Deploy tools and protocols for actively monitoring security threats, enabling swift detection and quick fix of any security issues.
- Educate users on security best practices and enforce adherence to established security policies to minimize the risk of data breaches or unauthorized access.
Framework Versions
Make sure that framework versions (such as Angular, React, .NET, Java, etc.) are kept up to date to ensure your analytics solution remains at the forefront of technology.
- Collaborate with your developers to address any compatibility issues arising from framework updates, ensuring a smooth transition to newer versions.
User Training
Empower users to utilize the BI solution through comprehensive training, including best practices for maximizing the value of the tool.
- Provide regular training sessions and resources to familiarize users with the BI tool’s functionalities.
- Foster a knowledge-sharing culture through user forums, knowledge-base articles, etc.
Continues Improvements
Continuous improvement is essential for ensuring that your embedded BI solution remains relevant, efficient, and aligned with the evolving needs of your organization. Establishing a feedback loop enables you to gather user input and implement enhancements to improve the BI solution over time.

Here are a few things you can do to ensure continued improvement:
- Vendor Engagement for Product Improvement: Check if the vendor provides a channel for product improvement. Feedback forms, user forums, and dedicated support channels are must-haves, allowing you to provide feedback and request new features to be added to the product.
- Visibility into Product Roadmaps and Backlogs: Find out if the vendor maintains public roadmaps and backlogs that provide visibility into planned features, enhancements, and bug fixes.
- Regular Product Review Meetings: Ask the vendor about the possibility of scheduling regular meetings or discussions to review product issues, discuss enhancement requests, and provide input on future product development efforts.
- Feedback Integration: Ensure that your feedback and feature requests are being added to the vendor’s roadmap and inquire about the estimated timeline for their implementation.
- Continuous Learning & Training: Stay updated on the BI solution’s new features and capabilities through regular training sessions and educational resources provided by the vendor. Empower your team with the knowledge and skills to effectively leverage these new features and capabilities.
About Reveal
Reveal is a leading embedded analytics solution that is purpose-built to provide ease of use for integrating powerful analytics capabilities into applications. With Reveal, you control branding, feature customization, security implementation, and deployment.
We bring industry knowledge, robust IT infrastructure, and domain expertise, allowing you to focus on your business growth while we handle the rest.
Explore Reveal:
- Book a Demo: See Reveal in action and discover how it can accelerate your business.
- Talk to an Expert: Schedule a call with our sales team to get answers to all your questions.
- Download our SDK: Experience firsthand how simple it is to integrate reliable self-service analytics into your existing website or application.
- Connect with our Senior Product Manager: Casey Ciniello, Reveal’s PM, is ready to address all your product-related inquiries.
- Join our Discord Channel: Our product team is available to assist with any questions or roadblocks you may encounter while using Reveal.
Unlock the full potential of embedded analytics with Reveal. Your data-driven future starts here.
